Insights
15 Cloud Security Challenges and Solutions You Must Know
Businesses today are storing data in the Cloud as it makes retrieving data easy and fast. Unfortunately, cloud solutions have also made data vulnerable to cyberattacks and cybercrimes.
Cyberattacks have increased in volume over the last few years, with 2021 registering some of the most intensive attacks ever witnessed. According to SonicWall’s 2022 Cyber Threat Report, every type of cyberattack increased in volume in 2021.
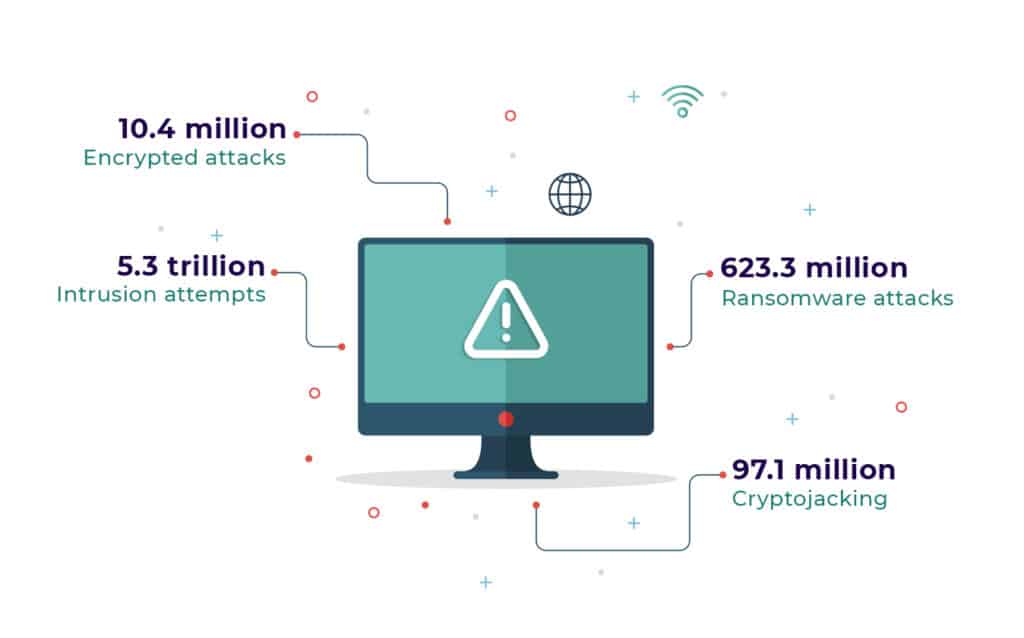
There were about 10.4 million encrypted attacks in 2021, apart from 623.3 million ransomware attacks. Cryptojacking saw 97.1 million attacks, and there were 5.3 trillion intrusion attempts.
We live in a world where cloud systems are unavoidable for business growth. The pandemic has furthered the need for businesses to move their data to the cloud. Organizations continue to expose themselves to security risks on the cloud due to poor understanding of cloud security, failing to meet compliances and outdated security policies.
Let us now take you through 15 cloud security risks and how you can avoid them.
1. Denial-of-Service Attacks:
Imagine a scenario where your existing customers cannot access a service(s) on your online platform. Apart from affecting sales, DoS attacks can dent your reputation. Hackers can overwhelm your network bandwidth, CPU, and RAM bringing your services to a halt.
Takeaways:
Monitoring network traffic using firewall and intrusion detection systems can help in raising timely alerts about unusual traffic. Site administrators also need to create DoS response plans to manage unwanted traffic on their sites.
2. Data Breaches:
‘Data is the new oil,’ and unsurprisingly, the bad guys are always after data. Unauthorized access to this data can result in loss of reputation and customer trust. It can negatively affect your business where your crucial account details are compromised.
Cloud Service Providers handle tons of data generated by businesses, and hence it is the favorite hunting ground for cybercriminals
Takeaways:
Protect your data with firewalls and encrypt data at every stage. Add a layer of security by embracing two-factor authentication.
3. Insufficient Access Management
Tools and data are exposed to attacks. Irrespective of the cloud service you use, you must accept this vulnerability. Unrestricted access to data and lack of an access management system can expose your business to unforeseeable risks and hurt your operations.
Takeaways:
Implement strict protocols and set strict guidelines on employees and clients who have access to data and the level of access. Restrict access to information on public Wi-Fi and unsecured devices.
4. Insider Threats:
This is a more significant threat than access management as it deals with people who have access to your data. This is a scenario where one of your employees’ abuses authorized access to the data on CSP’s (Cloud Service Provider) network. While it can be an honest and unintentional error by your employee, insider threat can be grievous when the employee provisions essential resources on the cloud to perform nefarious activities.
Takeaways:
Set strict guidelines on access and use of data on the cloud. Restrict downloading and sharing data outside your company’s network using messaging apps and personal emails. Strictly limit access to data and tools to employees and teams who need it.
5. Insecure APIs:
Application programming interfaces (APIs) are essential for cloud services as they let users customize their cloud experience in what is known as a management plan.
Unlike on-premises systems, cloud APIs are readily available, which exposes them to potential risk from cybercriminals. Threat actors can identify vulnerabilities of management APIs and exploit them.
Takeaways:
Your APIs must be designed with authentication, access control, and encryption following recommended best practices. Whenever possible, use standard API frameworks with proven security credentials instead of building one from scratch.
6. Misconfigured Cloud Storage:
This is one of the most common errors on the cloud. Cloud misconfiguration is when your cloud account hasn’t been configured according to the best practices, leaving the door open for hackers.
Takeaways:
Encrypt all data in the cloud by adhering to the best practices and restricting public access to the cloud. Avoid storing encryption passwords and their keys in an open repository.
7. Endpoint Security:
Endpoints are the user devices and web browsers used to access cloud accounts. Securing endpoints plays a crucial role in ensuring the overall security of your cloud systems. Much has evolved from the days when antivirus software was enough to protect browsers and systems.
Takeaways:
Ensure you have a sophisticated malware protection tool and firewall solutions to keep your browsers and devices safe. It is essential in the case of using LaaS and PaaS models.
8. Access Tokens and Policies:
Access tokens are used for applications to make API requests. They represent the authorization of specific applications to access a particular set of user data. To protect data, access tokens must be secured. Since they do not have any specific format – and can be any opaque string – they must only be understood by the resource server, authorization server, and to some extent by the application itself. If an HTTPS connection isn’t used, third parties can intercept Access Tokens.
Takeaways:
Access tokens shouldn’t last a lifetime. For maximizing security, it is best to use a combination of short-lived access tokens and long-lived refresh tokens.
9. Workload Security and Protection:
Securing endpoints is necessary, but they do not ensure all-encompassing security, especially for workloads across different cloud environments. Keeping the workload secured and protected has become ever so important in the rising threat of ransomware attacks, frequently targeting enterprises.
Takeaways:
Workload security through a protection platform is the advanced solution that secures server workloads both in public cloud infrastructure and in-service environments. CWPP (cloud workload protection platform) ensures that when multiple providers and customers are allowed in a cloud platform, workloads continue to remain secure.
10. VM Security:
Virtual machines can be attacked by viruses, ransomware, and malware. This can happen when an infected VM image or a user has access but little security training. Under a VM attack, the malware can spread across the virtual infrastructure unless adequate security measures are undertaken.
Takeaways:
Traditional security applications such as firewalls and antivirus protection can be used for virtualized security. The advantage of VM Security is that it can be applied to any specific security need.
11. Lack of Data Encryption:
A serious threat to cloud security is a data breach. Critical information like names, passwords, email addresses, and credit card numbers gets compromised because cybercriminals accessed the cloud account. A data breach can occur with malicious links and software, poorly designed network, presence of weak credentials, over permission, and improper configuration.
Takeaways:
The only way to reduce the risk of a data breach is through rigorous data encryption. Multi-factor authentication and data-at-rest encryption are solutions that ensure data encryption.
12. Compliance:
All organizations know what it means, but not all of them meet the compliance requirements on the cloud! Lack of awareness of the latest compliance requirements and oversights can often push your business into hot water, inviting legal challenges.
Takeaways:
Take compliance seriously and read user documents before signing up for any service. Make sure your team is in sync with the ever-changing compliance requirements and changes to privacy policies.
13. Secret Keys:
Are the privileged credentials that improve digital authentication. Database passwords, SSH keys, privileged account credentials, API keys, encryption keys, and private certificates are a few standard secret keys used. If care isn’t taken while encrypting secret keys, they can open the door for multiple security breaches.
Takeaways:
To ensure that all secret keys are safe, you must authenticate access requests, use role-based access controls, routinely rotate secrets, keep access policies constant, keep the audit trail through and remove secrets entirely from unprotected locations.
14. Security Threats on Applications:
Businesses increasingly rely on cloud-based applications for their day-to-day activities. But security threats continue to loom large. According to the 2020 Forrester report, most external attacks in 2019 were carried out by exploiting a software flaw or by compromising web applications.
Takeaways:
Securing cloud systems should not be an after-thought for developers. Integrated cybersecurity layers must be put in place to maximize security.
15. Network Layer Security:
Cloud network solutions have made life easier for businesses. New infrastructure can be added more efficiently without on-location IT teams, making the cloud systems more vulnerable.
Takeaways:
Educating employees and every user of your cloud environment is the first step towards network and cloud security. Dos and don’ts on security can be followed by developers and employees alike. There should also be adequate incident response plans to deal with untoward situations.
Conclusion
As more businesses move to the cloud, the threat scenario has also grown manifold. Cloud Service Providers work on the ‘shared responsibility model’ for data security. They provide you with a secured platform while sharing the onus for safety.
If your organization lacks the time and resources to implement the best practices of Cloud Security, Parker Digital can help. As experts in cloud security, we help organizations manage critical data and workloads on the cloud preventing data breaches and ensuring business continuity.
We provide you with consultancy, end-to-end security services, and more. Come on board and let us secure your cloud.

Published By
Ashish Dhawan
Director of Cybersecurity
As a visionary cybersecurity technology leader, Ashish has been working with mid-size & large organizations for the past 20 years on delivering successful security projects around cloud-native security, vulnerability management, cyberattack prevention, threat intelligence, security architecture, incident response, and global security risk management amongst many others.
With an outstanding record of establishing globally recognized cybersecurity frameworks, he works with executive leaders to deliver next-gen security solutions for today’s challenges.
Get in touch with us
Parkar Digital is a digital transformation and software engineering company headquartered in Atlanta, USA, and has engineering teams across India, Singapore, Dubai, and Latin America.
